IT assets↑
Select IT Assets from the main menu to view details about the scanned hosts, images, and applications that contribute to your cryptography inventory.
The tabs organize your scanned IT assets by:
- Hosts - a physical or virtualized computing system, such as a server, workstation, or virtual machine, that serves as the operating environment for applications and container images.
- Apps - a software program or service running on a host.
- Container images - a packaged software component that was scanned, containing an application’s filesystem and configuration.
- Files - any files that were uploaded through the AQG File Inspector.
The following sections provide details for each tab.
Hosts↑
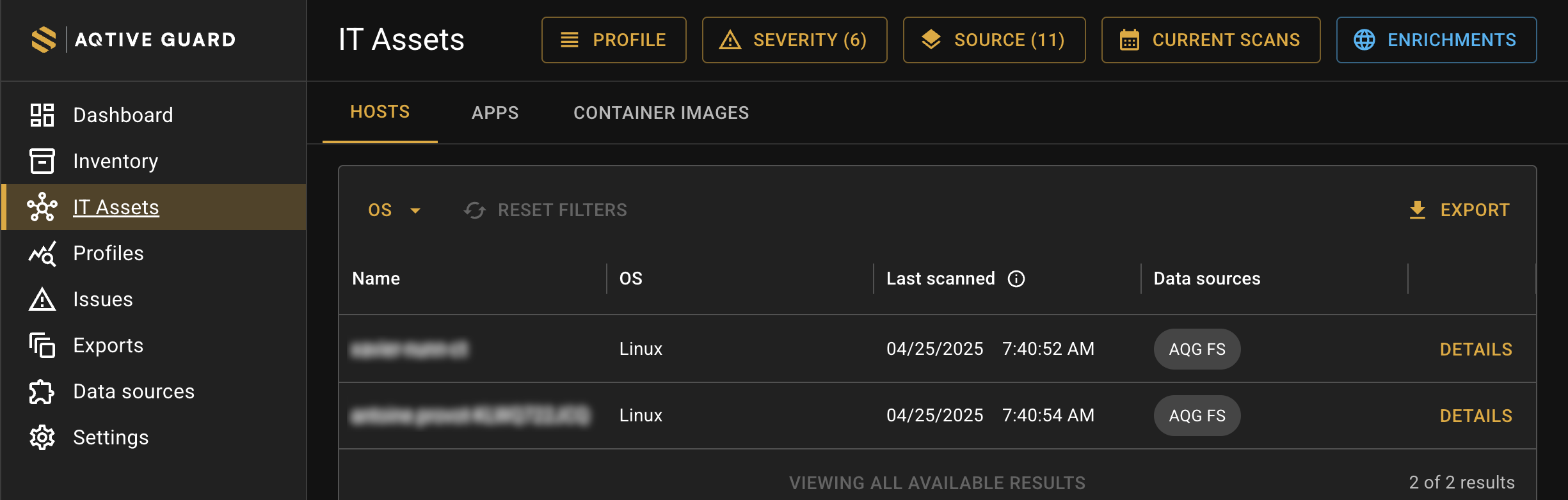
The Hosts tab provides an overview of your scanned laptops and servers, including:
- Name - the default or user-assigned name of the scanned host.
- OS - Operating System (Windows, Cygwin or Unix)
- Last scanned - the date and time of the most recent scan where the item was found (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Data sources - the integration or sensor that provided the data for the item.
Use the local filters at the top of the table to filter by host OS. You may also apply one or more global filters at the top of the screen.
Host details↑
Selecting Details provides an in-depth view of the cryptography discovered on the associated host, including:
- Keys - a sequence of bits used as input to a cryptographic algorithm to encrypt, decrypt, sign, or authenticate data.
- Certificates - a digitally signed document, linking a public key to an identity.
- Operations - a specific process or function, such as encryption, decryption, signing, or verification, that is performed on data using a key.
- Secrets - secrets are digital credentials providing identity authentication and authorizing access to privileged accounts, applications, and services.
- Apps - scanned software applications found on host.
- Sessions - the date, time, and data source(s) for a specific item that was ingested or detected, providing a detailed breakdown of its Last scanned history.
Within the details panel, you can also select View full host to access a JSON object containing all host metadata.
Apps↑
The Apps tab presents information about scanned applications, including:
- Name - the application name, as provided by the data source. For application data uploaded from CBOM, this is the user-provided name of the application or codebase that this CBOM data belongs to, typically referencing the root name of the codebase.
- Language - the programming language used for the application, as provided by the CBOM or the tool used to scan the application.
- Last scanned - the date and time of the most recent scan where the item was found (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Data sources - the integration or sensor that provided the data for the item.
You may apply one or more global filters at the top of the screen.
App details↑
Selecting Details provides an in-depth view of the cryptography discovered in the application, including:
- Keys - a sequence of bits used as input to a cryptographic algorithm to encrypt, decrypt, sign, or authenticate data.
- Certificates - a digitally signed document, linking a public key to an identity.
- Operations - a specific process or function, such as encryption, decryption, signing, or verification, that is performed on data using a key.
- Secrets - container secrets are digital credentials providing identity authentication and authorizing access to privileged accounts, applications, and services.
- Hosts - scanned laptops and servers where this app was detected.
- Sessions - the date, time, and data source(s) for a specific item that was ingested or detected, providing a detailed breakdown of its Last scanned history.
Within the details panel, you can also select View full application to access a JSON object containing all application metadata.
Container images↑
The Container images tab displays the following information for scanned container images:
- Image ID - the name assigned to the image at creation, as supplied by the data source.
- Repository - the storage location of the container image, such as a Git repository.
- Layer SHA - the hash or digest for the scanned container layer.
- Last scanned - the date and time of the most recent scan where the item was found (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Data sources - the integration or sensor that provided the data for the item.
You may also apply one or more global filters at the top of the screen.
Container image details↑
Selecting Details provides an in-depth view of the cryptography discovered in the associated image, including:
- Keys - a sequence of bits used as input to a cryptographic algorithm to encrypt, decrypt, sign, or authenticate data.
- Certificates - a digitally signed document, linking a public key to an identity.
- Operations - a specific process or function, such as encryption, decryption, signing, or verification, that is performed on data using a key.
- Secrets - container secrets are digital credentials providing identity authentication and authorizing access to privileged accounts, applications, and services.
- Sessions - the date, time, and data source(s) for a specific item that was ingested or detected, providing a detailed breakdown of its Last scanned history.
Within the details panel, you can also select View full container to access a JSON object containing all container metadata.
Files↑
The Files tab displays the following information for files uploaded through the AQG File Inspector:
- Name - the name of the uploaded file.
- Last scanned - the date and time of the most recent scan where the item was found (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Data sources - the integration or sensor that provided the data for the item.
You may apply one or more global filters at the top of the screen.
File details↑
Selecting Details provides an in-depth view of the cryptography discovered on the associated file, including:
- Keys - a sequence of bits used as input to a cryptographic algorithm to encrypt, decrypt, sign, or authenticate data.
- Certificates - a digitally signed document, linking a public key to an identity.
- Sessions - the date, time, and data source(s) for a specific item that was ingested or detected, providing a detailed breakdown of its Last scanned history.
Within the details panel, you can also select View full file to access a JSON object containing all file metadata.
Export IT Asset views↑
Selecting the Export button opens the Exports page, where you’ll enter export information. For details, refer to Exports.