Inventory↑
Select Inventory from the main menu to view detailed, itemized lists of your discovered cryptography.
The tabs organize your cryptography by:
- Keys - a sequence of bits used as input to a cryptographic algorithm to encrypt, decrypt, sign, or authenticate data.
- Certificates - a digitally signed document, linking a public key to an identity.
- Operations - a specific process or function, such as encryption, decryption, signing, or verification, that is performed on data using a key.
- TLS configs - an inventory object that summarizes all connections received by a server or IP address.
- Handshakes - processes to establish a secure connection between networked applications.
- Secrets - non-standard or user-defined objects retrieved from an external data source.
- Hosts - a physical or virtualized computing system, such as a server, workstation, or virtual machine, that serves as the operating environment for applications and container images.
- Apps - a software program or service running on a host.
- Container images - a packaged software component that was scanned, containing an application’s filesystem and configuration.
- Files - any files that were uploaded through the AQG File Inspector.
The following sections provide details for each tab.
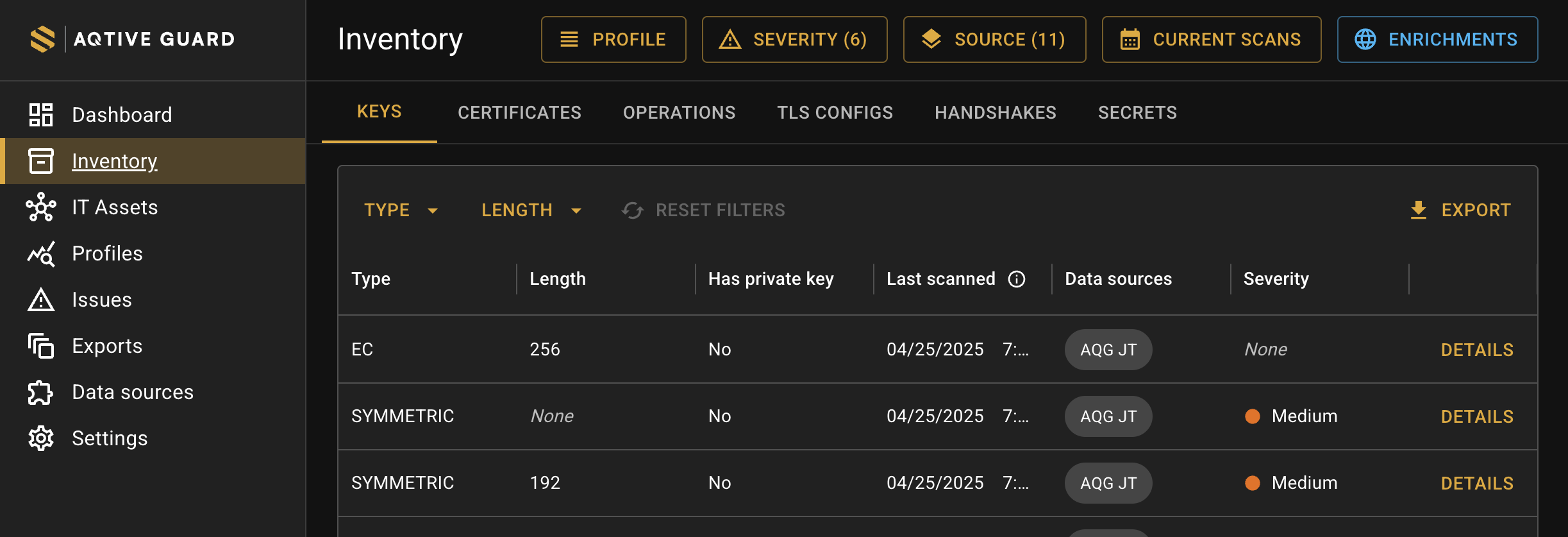
Keys↑
The Keys tab provides a comprehensive view of the keys within your cryptography inventory, including the following information for each:
- Type - the algorithm used to generate the key, such as RSA, DSA, DH, etc.
- Length - the length of the key, in bits (1024, 2048, etc.)
- Has private key - indicates whether the key has an associated private key.
- Last scanned - the date and time of the most recent scan where the object was found (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Data sources - the integration or sensor that provided the data for the item.
- Severity - when applicable, indicates the degree of non-compliance with policy as determined by the rule used for analysis.
Use the local filters at the top of the table to filter by key Type or key Length. You may also apply one or more global filters at the top of the screen.
Key details↑
To view more detailed information about a specific key, select Details. The details panel provides additional insights, including associated:
- Locations - where the item was discovered.
- Issues - generated when a rule flags the item.
- Certificates - a digitally signed document, linking a public key to an identity.
- Operations - a specific process or function, such as encryption, decryption, signing, or verification, that is performed on data using a key.
- TLS configs - a summary of all connections received by a server or IP address, with data sourced from inferred handshakes or third-party active scans.
- Hosts - a physical or virtualized computing system, such as a server, workstation, or virtual machine, that serves as the operating environment for applications and container images.
- Apps - a software program or service running on a host.
- Container images - a packaged software component that was scanned, containing an application’s filesystem and configuration.
- Sessions - the date, time, and data source(s) for a specific item that was ingested or detected, providing a detailed breakdown of its Last scanned history.
To access a JSON object containing all key metadata, scroll to the bottom of the panel and select View full key.
Certificates↑
The certificate inventory is summarized in the Certificates tab, which includes the following information:
- Subject - the entity that this certificate represents, e.g. web site, application, individual.
- Issuer - the authority that issued the certificate.
- Valid until - the certificate expiration date.
- Validity period - the certificate validity period.
- Digest algorithm - the hash function used.
- Last scanned - the date and time of the most recent scan where the object was found (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Data sources - the integration or sensor that provided the data for the item.
- Severity - when applicable, indicates the degree of non-compliance with policy as determined by the rule used for analysis.
Use the local filters at the top of the table to filter by certificate Subject or Issuer. You may also apply one or more global filters at the top of the screen.
Certificate details↑
To view more detailed information about a specific certificate, select Details. The details panel provides additional insights, including associated:
- Locations - where the item was discovered.
- Issues - generated when a rule flags the item.
- Keys - a sequence of bits used as input to a cryptographic algorithm to encrypt, decrypt, sign, or authenticate data.
- Operations - a specific process or function, such as encryption, decryption, signing, or verification, that is performed on data using a key.
- TLS configs - a summary of all connections received by a server or IP address, with data sourced from inferred handshakes or third-party active scans.
- Handshakes - processes to establish a secure connection between networked applications.
- Hosts - a physical or virtualized computing system, such as a server, workstation, or virtual machine, that serves as the operating environment for applications and container images.
- Apps - a software program or service running on a host.
- Container images - a packaged software component that was scanned, containing an application’s filesystem and configuration.
- Sessions - the date, time, and data source(s) for a specific item that was ingested or detected, providing a detailed breakdown of its Last scanned history.
To access a JSON object containing all certificate metadata, scroll to the bottom of the panel and select View full certificate.
Operations↑
The Operations tab provides a comprehensive view of the cryptographic operations discovered during analysis, including the following information:
- Type - the cryptographic operation performed.
- Timestamp - the date and time of the operation (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Algorithms - the algorithm used, such as AES, RSA, HMAC, etc.
- Last scanned - the date and time of the most recent scan where the object was found (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Data sources - the integration or sensor that provided the data for the item.
- Severity - when applicable, indicates the degree of non-compliance with policy as determined by the rule used for analysis.
Note
If an operation involves multiple calls, the timestamp of the operation reflects the final call.
Use the local filters at the top of the table to filter by operation Type. You may also apply one or more global filters at the top of the screen.
Operations details↑
To view more detailed information about a specific operation, select Details. The details panel provides additional insights, including associated:
- Stack trace - the sequence of function calls at the point the item was detected.
- Issues - generated when a rule flags the item.
- Keys - a sequence of bits used as input to a cryptographic algorithm to encrypt, decrypt, sign, or authenticate data.
- Certificates - a digitally signed document, linking a public key to an identity.
- Hosts - a physical or virtualized computing system, such as a server, workstation, or virtual machine, that serves as the operating environment for applications and container images.
- Apps - a software program or service running on a host.
- Container images - a packaged software component that was scanned, containing an application’s filesystem and configuration.
- Sessions - the date, time, and data source(s) for a specific item that was ingested or detected, providing a detailed breakdown of its Last scanned history.
To access a JSON object containing all operations metadata, scroll to the bottom of the panel and select View full operation.
TLS configs↑
The TLS configs tab provides a comprehensive view of how your systems are configured to use the Transport Layer Security (TLS) protocol on the server side. It includes:
- IP address - the network address of the host.
- Port - The specific port number used on the host for the connection.
- Protocol - the transport protocol used, such as TCP, UDP, etc.
- Supported versions - the TLS versions that have been observed through successful handshakes.
- Unsupported versions - the TLS versions that have been actively confirmed to not be supported. This data can only be reported by Qualys due to its active scanning approach.
- Last scanned - the date and time of the most recent scan where the object was found (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Data sources - the integration or sensor that provided the data for the item.
- Severity - when applicable, indicates the degree of non-compliance with policy as determined by the rule used for analysis.
Use the local filters at the top of the table to filter by IP address, Supported versions or Unsupported versions. You may also apply one or more global filters at the top of the screen.
TLS config IP address filtering↑
IP address filtering helps you control the data displayed in the TLS configs view. You can specify IP addresses and network ranges using standard CIDR notation.
Note
Only standard CIDR notation such as /24 or /13 is supported for subnet masking. Other non-standard or alternative subnet masking formats, such as hyphen-notation, aren’t supported.
Filtering options↑
- Include: Display only the specified IP addresses or ranges.
- Exclude: Remove the specified IP addresses or IP ranges. This is particularly useful for excluding irrelevant or out-of-scope assets from your view.
Note
IP address filtering doesn’t support wildcard characters (for example 192.168.1.*) for defining IP addresses or ranges.
Filter TLS configs by IP address↑
- Select Inventory from the main menu, then select TLS configs.
- Select the IP address dropdown.
- Enter a specific IP address, or an IP range using CIDR notation that you’re interested in filtering.
- Select either Include to include this IP address or range, or Exclude to exclude it.
- Select + to add another IP address or range. You can also select Reset to clear all entered filters and start again.
- Select Apply.
Example
When applying multiple IP address filters (include or exclude), the system operates using AND logic. This means that all specified inclusion and exclusion conditions must be met simultaneously for an IP address to be displayed.
For instance, if you include 10.0.0.0/8 and exclude 10.1.1.0/24, only IP addresses within the 10.0.0.0/8 range that are not within 10.1.1.0/24 will be shown.
TLS config details↑
To view more detailed information about a specific TLS config, select Details. The details panel provides additional insights, including associated:
- Server supported ciphersuites - the ciphersuites the server has been confirmed to support during the scanned handshake.
- Server supported key exchange algorithms - the key exchange protocols the server has been confirmed to support during the scanned handshake.
- Server supported server authentication algorithms - the authentication protocols the server has been confirmed to support during the scanned handshake.
- Handshakes - TLS negotiations of cryptographic algorithms relative to this server that have been captured.
- Issues - generated when a rule flags the item.
- Certificates - cryptographic documents that the server uses to authenticate itself. The full trust chain is extracted.
- Keys - the cryptographic keys extracted from the certificates.
- Sessions - the date, time, and data source(s) for a specific item that was ingested or detected, providing a detailed breakdown of its Last scanned history.
To access a JSON object containing all TLS config metadata, scroll to the bottom of the panel and select View full TLS config.
Handshakes↑
The Handshakes tab provides details about the negotiation of cryptographic parameters during data transmission:
- Source IP - the IP address of the host that initiated the connection.
- Target IP - the IP address of the destination host.
- TLS Version - the version of Transport Layer Security used.
- Selected ciphersuite - the ciphersuite selected for use in this connection.
- Min. client TLS Version - the earliest version of TLS that the client will accept.
- Status - whether the handshake was performed successfully or not.
- Target port - the port number used by the target host to receive the connection.
- Last scanned - the date and time of the most recent scan where the object was found (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Data sources - the integration or sensor that provided the data for the item.
- Severity - when applicable, indicates the degree of non-compliance with policy as determined by the rule used for analysis.
Use the local filters at the top of the table to filter by Source IP address or Target IP address. Refer to Handshake IP address filtering for details.
You may also apply one or more global filters at the top of the screen.
Handshake IP address filtering↑
IP address filtering for handshakes works the same way as it does for TLS configs, with the option to filter on either the Source IP address, the Target IP address, or both.
For details, refer to TLS config IP address filtering.
Handshake details↑
To view more detailed information about a specific handshake, select Details. The details panel provides additional insights, including associated:
- Client supported ciphersuites - the ciphersuites the client indicated it could support during the scanned handshake.
- Client supported key exchange algorithms - the key exchange protocols the client indicated it could support during the scanned handshake.
- Client supported server authentication algorithms - the authentication protocols the client indicated it could support during the scanned handshake.
- Client supported versions - the security protocol versions, such as TLS 1.2 or TLS 1.3, the client indicated it could support during the scanned handshake.
- Issues - generated when a rule flags the item.
- Certificates - a digitally signed document, linking a public key to an identity.
- TLS configs - a summary of all connections received by a server or IP address, with data sourced from inferred handshakes or third-party active scans.
- Sessions - the date, time, and data source(s) for a specific item that was ingested or detected, providing a detailed breakdown of its Last scanned history.
Note
An ‘UNKNOWN’ value in a handshake indicates AQG was unable to translate a numerical identifier (NID) due to missing data, a non-standard NID, or a recently introduced NID.
To access a JSON object containing all handshake metadata, scroll to the bottom of the panel and select View full handshake.
Secrets↑
The Secrets tab displays an inventory of non-standard or user-defined objects retrieved from an external data source.
- Type - the secret type.
- Last scanned - the date and time of the most recent scan where the object was found (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Data sources - the integration or sensor that provided the data for the item.
- Severity - when applicable, indicates the degree of non-compliance with policy as determined by the rule used for analysis.
You may apply one or more global filters at the top of the screen.
Secrets details↑
To view more detailed information about a specific operation, select Details. The details panel provides additional insights, including associated:
- Locations - where the item was discovered.
- Issues - generated when a rule flags the item.
- Hosts - a physical or virtualized computing system, such as a server, workstation, or virtual machine, that serves as the operating environment for applications and container images.
- Apps - a software program or service running on a host.
- Container images - a packaged software component that was scanned, containing an application’s filesystem and configuration.
- Sessions - the date, time, and data source(s) for a specific item that was ingested or detected, providing a detailed breakdown of its Last scanned history.
To access a JSON object containing all secrets metadata, scroll to the bottom of the panel and select View full secret.
Hosts↑
The Hosts tab provides an overview of your scanned laptops and servers, including:
- Name - the default or user-assigned name of the scanned host.
- OS - Operating System (Windows, Cygwin or Unix)
- Last scanned - the date and time of the most recent scan where the item was found (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Data sources - the integration or sensor that provided the data for the item.
Use the local filters at the top of the table to filter by host OS. You may also apply one or more global filters at the top of the screen.
Host details↑
Selecting Details provides an in-depth view of the cryptography discovered on the associated host, including:
- Keys - a sequence of bits used as input to a cryptographic algorithm to encrypt, decrypt, sign, or authenticate data.
- Certificates - a digitally signed document, linking a public key to an identity.
- Operations - a specific process or function, such as encryption, decryption, signing, or verification, that is performed on data using a key.
- Secrets - secrets are digital credentials providing identity authentication and authorizing access to privileged accounts, applications, and services.
- Apps - scanned software applications found on host.
- Sessions - the date, time, and data source(s) for a specific item that was ingested or detected, providing a detailed breakdown of its Last scanned history.
Within the details panel, you can also select View full host to access a JSON object containing all host metadata.
Apps↑
The Apps tab presents information about scanned applications, including:
- Name - the application name, as provided by the data source. For application data uploaded from CBOM, this is the user-provided name of the application or codebase that this CBOM data belongs to, typically referencing the root name of the codebase.
- Language - the programming language used for the application, as provided by the CBOM or the tool used to scan the application.
- Last scanned - the date and time of the most recent scan where the item was found (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Data sources - the integration or sensor that provided the data for the item.
You may apply one or more global filters at the top of the screen.
App details↑
Selecting Details provides an in-depth view of the cryptography discovered in the application, including:
- Keys - a sequence of bits used as input to a cryptographic algorithm to encrypt, decrypt, sign, or authenticate data.
- Certificates - a digitally signed document, linking a public key to an identity.
- Operations - a specific process or function, such as encryption, decryption, signing, or verification, that is performed on data using a key.
- Secrets - container secrets are digital credentials providing identity authentication and authorizing access to privileged accounts, applications, and services.
- Hosts - scanned laptops and servers where this app was detected.
- Sessions - the date, time, and data source(s) for a specific item that was ingested or detected, providing a detailed breakdown of its Last scanned history.
Within the details panel, you can also select View full application to access a JSON object containing all application metadata.
Container images↑
The Container images tab displays the following information for scanned container images:
- Image ID - the name assigned to the image at creation, as supplied by the data source.
- Repository - the storage location of the container image, such as a Git repository.
- Layer SHA - the hash or digest for the scanned container layer.
- Last scanned - the date and time of the most recent scan where the item was found (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Data sources - the integration or sensor that provided the data for the item.
You may also apply one or more global filters at the top of the screen.
Container image details↑
Selecting Details provides an in-depth view of the cryptography discovered in the associated image, including:
- Keys - a sequence of bits used as input to a cryptographic algorithm to encrypt, decrypt, sign, or authenticate data.
- Certificates - a digitally signed document, linking a public key to an identity.
- Operations - a specific process or function, such as encryption, decryption, signing, or verification, that is performed on data using a key.
- Secrets - container secrets are digital credentials providing identity authentication and authorizing access to privileged accounts, applications, and services.
- Sessions - the date, time, and data source(s) for a specific item that was ingested or detected, providing a detailed breakdown of its Last scanned history.
Within the details panel, you can also select View full container to access a JSON object containing all container metadata.
Files↑
The Files tab displays the following information for files uploaded through the AQG File Inspector:
- Name - the name of the uploaded file.
- Last scanned - the date and time of the most recent scan where the item was found (
MM/DD/YYYY HH:MM:SS AM/PM), based on the time zone set in your browser, with system time in UTC. - Data sources - the integration or sensor that provided the data for the item.
You may apply one or more global filters at the top of the screen.
File details↑
Selecting Details provides an in-depth view of the cryptography discovered on the associated file, including:
- Keys - a sequence of bits used as input to a cryptographic algorithm to encrypt, decrypt, sign, or authenticate data.
- Certificates - a digitally signed document, linking a public key to an identity.
- Sessions - the date, time, and data source(s) for a specific item that was ingested or detected, providing a detailed breakdown of its Last scanned history.
Within the details panel, you can also select View full file to access a JSON object containing all file metadata.
Export Inventory views↑
Selecting the Export button opens the Exports page, where you’ll enter export information. For details, refer to Exports.